To connect your server externally with different services and applications, Devrims provides an option to add any port on which service or application will communicate. You can add any network port except those reserved by services offered by Devrims for external communication with the server and add your desired access policy. This article will explain how to add and manage new and existing network ports.
1) What are Security Rules on Port?
Security Rules are the access policies to allow or block external connection(s) to communicate with any services, packages or applications deployed on your server. All traffic is blocked by default on newly added ports until you will not add any security rule. You can allow specific IP addresses, allow all IPs and block IPs if all IPs are allowed.
Let’s take an example of reserved port # 2222 used by SSH to take the remote connection of the server. By default, our platform allows all traffic on port # 2222 used by SSH on every server, but you can deploy your own security rule and remove the existing one.
2) How to Add New Port?
- Login to your Devrims platform using your credentials to add a new port.
- Select a server from the server listing screen.
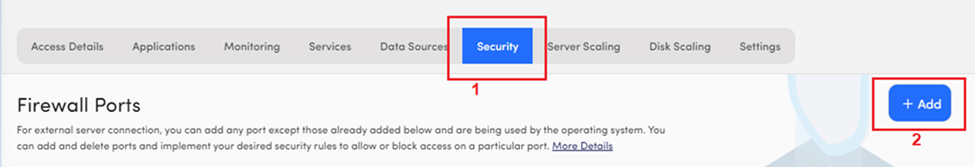
- Click on the Security tab.
- To add a new port, click on the + Add button available on the right side under Server Tabs.
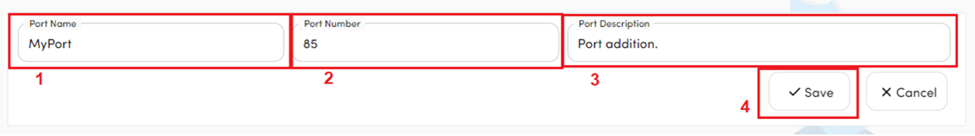
- Enter the Port Name, Number and Description.
- Click on the Save button.
You can add any port from 0 to 65535 except the system reserved port. Once the port is added, you can add the security rule.
3) How to Add Security Rule?
To add Security Rule:
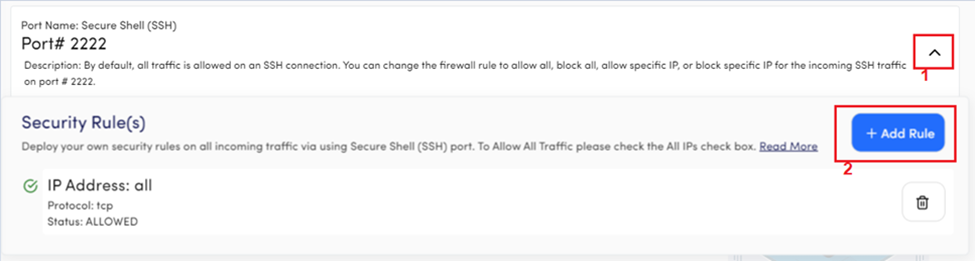
- Click on the drop-down arrow placed on the right side of the card.
- Click on the + Add Rule button.
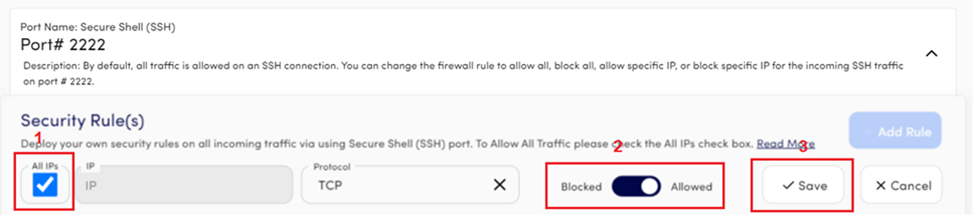
To allow All IPs:
- Click on the check box of All IPs and the system will automatically select the Allowed states of the toggle button.
- Select the Network protocol, whether TCP or UDP, from the drop-down menu of Protocol.
- Click on the Save button to add the rule.
Kindly note you can’t add the Blocked All security rule because, by default, All IPs are blocked if the Allowed All rule is not added. If the Allowed All IPs rule is already added and you want to block all traffic, simply delete the Allowed All IPs rule to block All IPs.
Let’s discuss the second case in which you want to block a specific IP address.
- Enter the IP address.
- Select the connection protocol.
- Click on the Save button to block a specific IP.
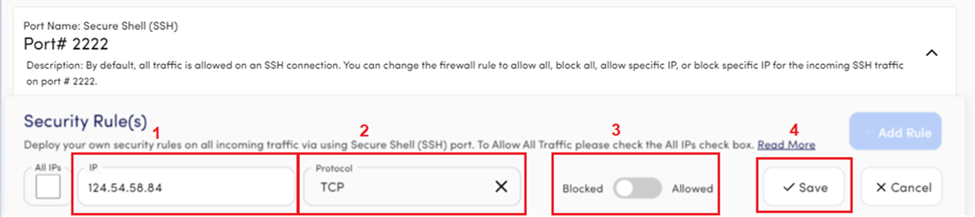
The third most crucial case is only to Allow specific IP addresses.
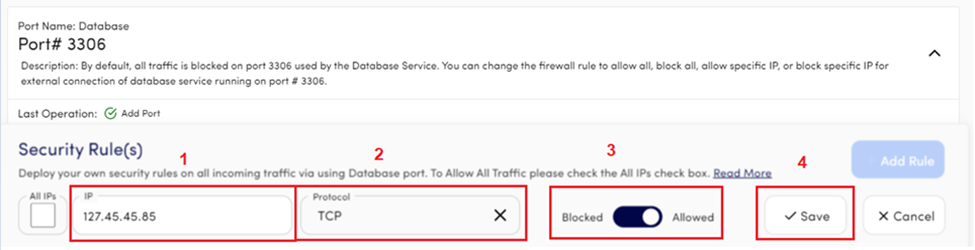
For example, you want to connect the database running on the Devrims server with any external application hosted on a different server. In this case:
- Add the public IP address of the application server on the database port, which is 3306.
- Select the TCP protocol.
- Click the Save button.
Via adding this rule, your application can easily access the database running on the Devrims server.
4) System Reserved Ports and Its Default Security Rule
You can add multiple ports based on your requirement from port number 0 to 65535, but some ports are already reserved for different services offered via the Devrims dashboard.
This section will discuss all reserved ports of the server and its default rule.
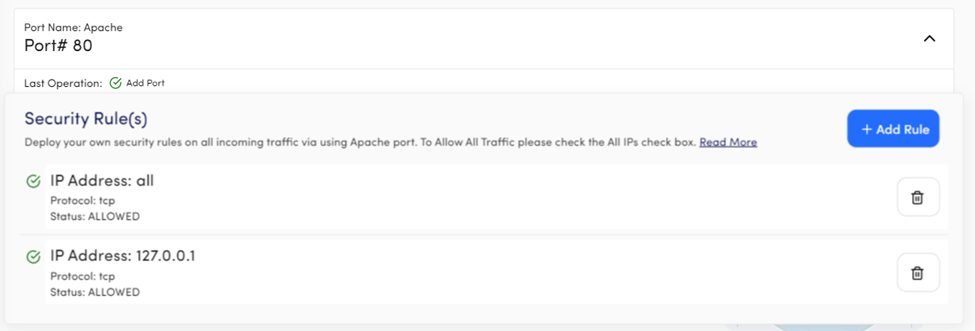
Port Name: Apache or Nginx
Port# 80
Description: Port 80 is reserved for web servers, either Apache or Nginx, for http communication with default security rule Allowed All, so your website can be accessible over the web. Kindly note that if you delete the Allow All rule, your website will not be accessible over the web. If your website is under development and you don’t want anyone to access it, remove the Allowed All rule and Allow your IP only to access the website.
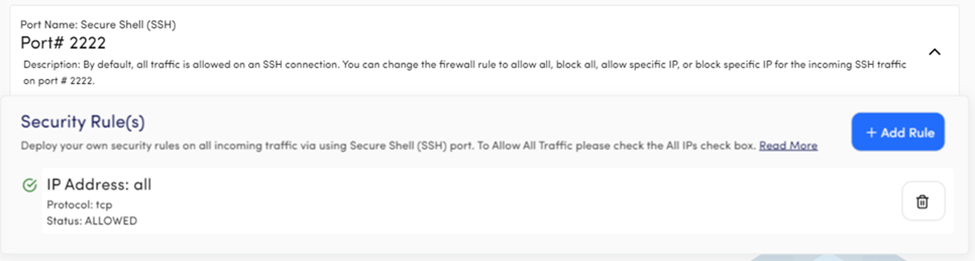
Port Name: Secure Shell (SSH)
Port Number: 2222
Description: You can take access to your server with any third-party SSH client. Our system used 2222 port to establish an SSH connection and the port is enabled in every server launched via Devrims dashboard. The default security rule of the SSH port is Allow All, but you can change it anytime.
Your server is protected via a brute force attack via SSH because the system will block the IP addresses on three false attempts to access the server. In case, by mistake, if you try to take SSH connection of your server with the wrong password, the system will block your IP address on a third false attempt. If the system blocks your IP address, please allow your IP address in the security rule, so the system will mark your IP address in the whitelist and never block your IP in the future.
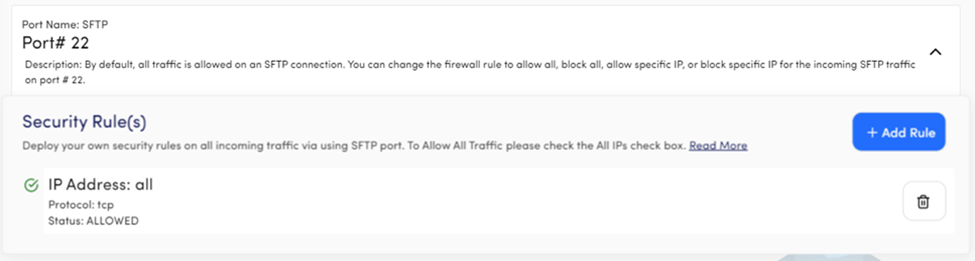
Port Name: SFTP
Port# 22
Description: Devrims offer Secure File Transfer Protocol(SFTP), which is more secure than traditional File Transfer Protocol, so you share and transfer the files between your server and any other machine. Port 22 is reserved for SFTP with the default security rule Allowed All, but you can remove the default security rule and add your own. Your server is protected via a brute force attack on the SFTP port because the system will block the IP addresses on three false attempts to take server access via SFTP.
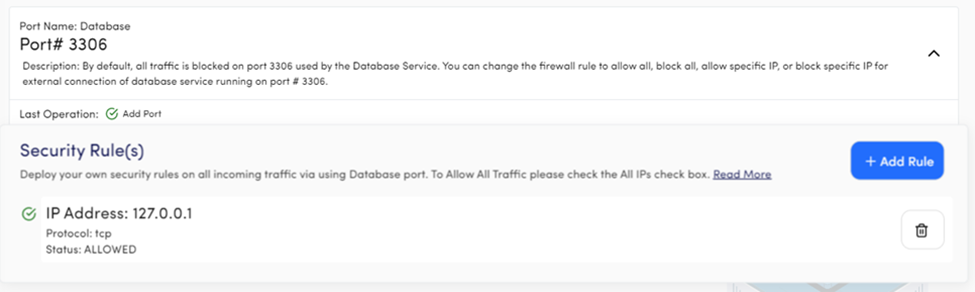
Port Name: Database
Port# 3306
Description: Port 3306 is reserved for MySQL database service with Blocked All security rule. You can add any rule on the database port to connect your database externally.
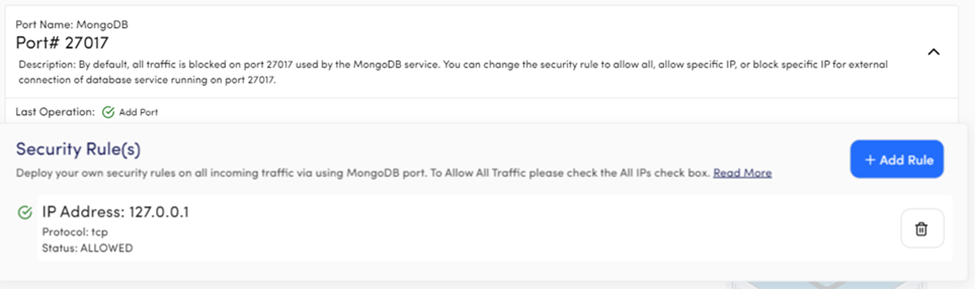
Port Name: MongoDB
Port# 27017
Description: Port 27017 is reserved for MongoDB database service with Blocked All security rule. You can add any rule or change the existing one as per your requirement.
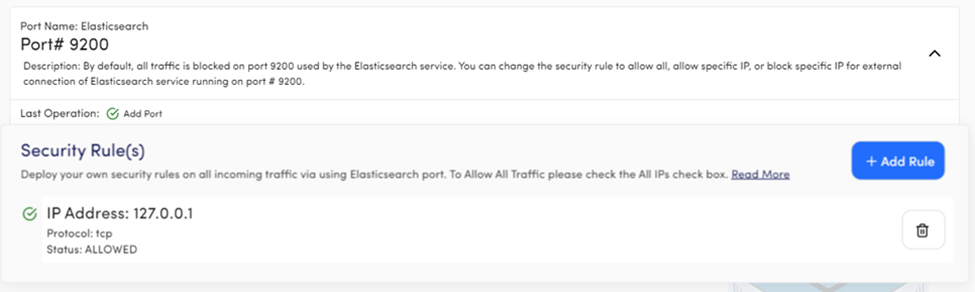
Port Name: Elasticsearch
Port# 9200
Description: Port 9200 is reserved for MongoDB database service with Blocked All security rule. You can add any rule or change the existing one as per your requirement.
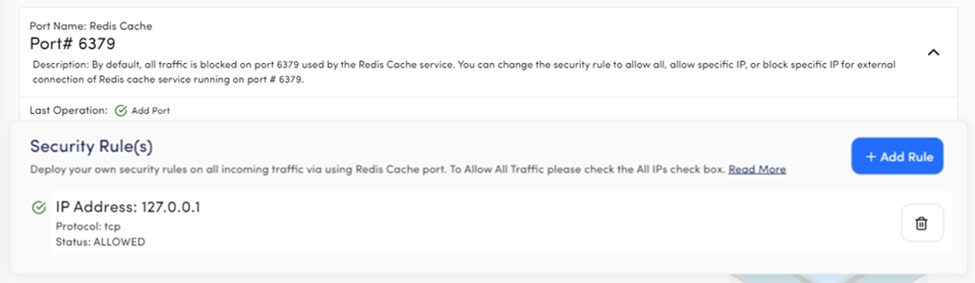
Port Name: Redis Cache
Port# 6379
Description: Port 6379 is reserved for Redis Cache service with Blocked All security rule. You can add any rule or change the existing one as per your requirement.
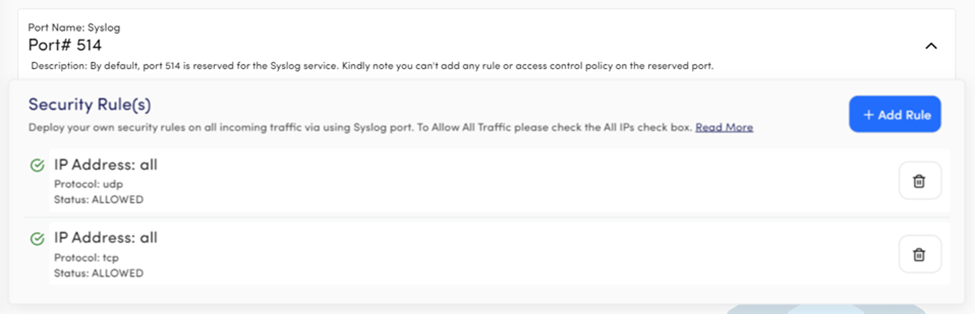
Port Name: Syslog
Port# 514
Description: Port 514 is used by Syslog and the users can’t change or add the security rule.
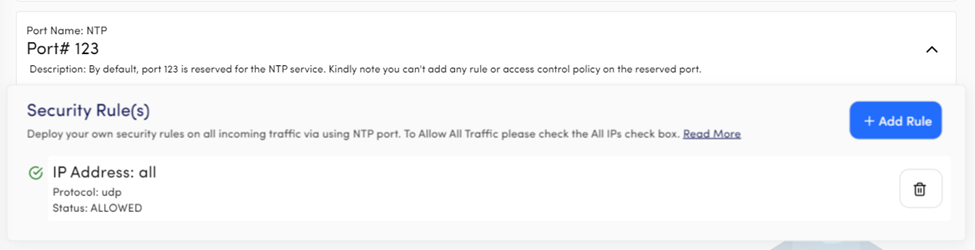
Port Name: NTP
Port# 123
Description: Port 123 is used by Network Time Protocol (NTP), and the users can’t change or add the security rule.
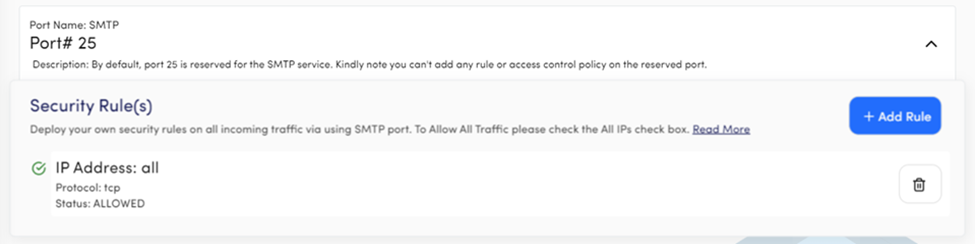
Port Name: SMTP
Port# 25
Description: Port 25 is used by SMTP for email communication and the users can’t change or add the security rule.
Note: I hope this article will help you manage your server’s network ports and security. If you face any issues or need further help, kindly contact our support on Live Chat or create a ticket from Devrims Dashboard.

